Des Uses Which of the Following Encryption Key Length
At the decryption site DES takes a 64-bit ciphertext and creates a 64-bit block of plaintext. In general longer keys provide stronger encryption.

What Is An Encryption Key Definition From Searchsecurity
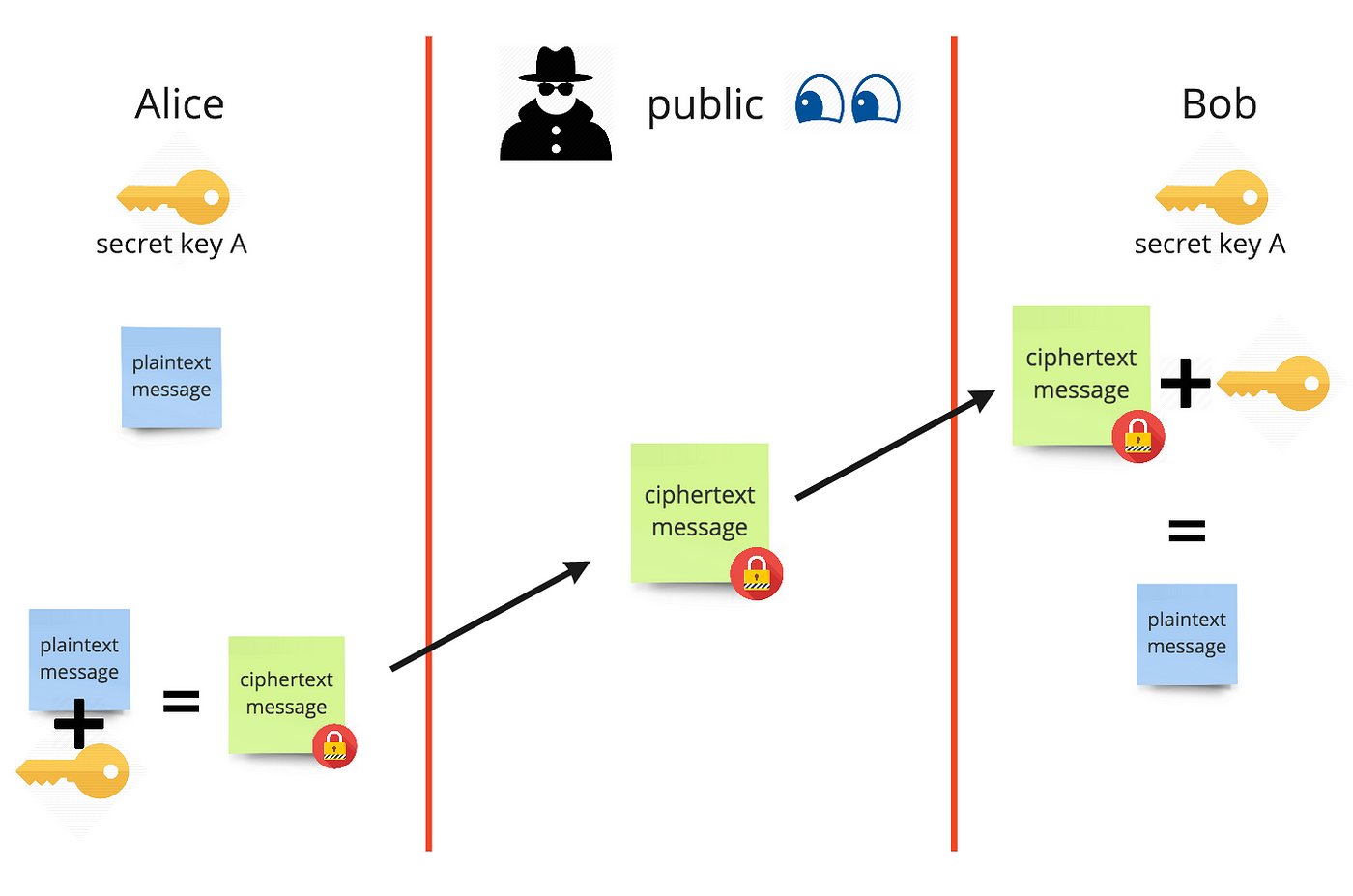
Key values must be the same length as the message.
. DES uses 16 rounds of the Feistel structure using a different key for each round. Established as a standard in 1977. The 128-bit key size has ten rounds the 192-bit key size has 12 rounds and the 256-bit key size has 14 rounds.
Key values must be protected from physical disclosure. 64-bit Key DES actually uses a 64-bit key however eight of those bits are utilized for checks making the effective length to only 56 bits. The encryption process is time-consuming.
The Data Encryption Standard DES ˌ d iː ˌ iː ˈ ɛ s d ɛ z is a symmetric-key algorithm for the encryption of digital data. Has the key length of 56 bits. A key factor to keep in mind is that guessing is better than not answering a question.
D Trojan Horse 71. Encryption strength is often described in terms of the size of the keys used to perform the encryption. What type of key or keys are used in symmetric cryptography.
Which of the following is not a block cipher operating mode. To prevent this from happening double DES and triple DES were introduced which are much more secured than the original DES because it uses 112 and 168 bit keys respectively. The same 56-bit cipher key is used for both encryption and decryption.
Can be used for digital signatures encryption and key management. In cryptography key size key length or key space refer to the number of bits in a key used by a cryptographic algorithm such as a cipher. Can be used to implement Diffie-Hellman El Gamal or Schnorr public key algorithms b.
DES became the approved federal encryption standard in November 1976 and was subsequently reaffirmed as the standard in 1983 1988 and 1999. For example 128-bit keys for use with the RC4 symmetric-key cipher supported by SSL provide significantly better cryptographic protection than 40-bit keys for use with the same cipher. Key values must be random.
A logarithmic measure of the fastest known attack against an algorithm since the security of all algorithms can be violated by brute-force attacks. DES is based on the Feistel block cipher called LUCIFER developed in 1971 by IBM cryptography researcher Horst Feistel. Private keys used to encrypt and decode cardholder data should always be stored in one or more of the following forms according to PCI DSS requirement 353 for secure key management and key storage.
CISSP - Question Bank 09. The cryptanalysts from the United States discovered a pattern in the method the Soviets used to generate their onetime pads. The block size can be of 128 192 or 256 bits depending upon the key length.
DES uses a 64-bit key but because eight of those bits are used for parity checks the effective key length is only 56 bits. 61 Encryption and decryption with DES At the encryption site DES takes a 64-bit plaintext and creates a 64-bit ciphertext. Key length defines the upper-bound on an algorithms security ie.
Not suitable for hardware applications d. Although its short key length of 56 bits makes it too insecure for applications it has been highly influential in the advancement of cryptography. Kerberos is an authentication scheme that can be used for a Public key cryptography b Digital signature c Hash function d Single sign on 73.
Reduce cipher complexity Weak keys can be avoided at key generation. After this pattern was discovered. The block size is 64 bits.
All but which of the following are true regarding elliptic curve cryptosystems ECC. So it treats the 128-bit block size as 16 bytes during the encryption procedure. It offers key lengths of 128 192 and 256 bits.
Smaller key sizes used in ECC can result in higher levels of security than larger non-ECC algorithms c. The encryption algorithm generates 16 different 48-bit subkeys one for each of the 16 encryption rounds. In cryptography Triple DES 3DES or TDES officially the Triple Data Encryption Algorithm TDEA or Triple DEA is a symmetric-key block cipher which applies the DES cipher algorithm three times to each data block.
As we know the Data encryption standard DES uses 56 bit key to encrypt any plain text which can be easily be cracked by using modern technologies. It should be encrypted and stored separately from the data encryption key with a key encryption key that is at least as strong as the data. The algorithm for encryption products 16 different subkeys of 48 bits each.
Double DES and Triple DES. How Does AES Work. Which of the following is the weakest symmetric encryption method.
Hence accounts that can use DES to authenticate to services are at significantly greater risk of having that accounts logon sequence decrypted and the account compromised. Each Question Bank includes 20 practice questions that have been designed to measure your knowledge of key ideas. DES has 4 weak keys 01010101 01010101 FEFEFEFE.
The number of rounds to be carried out depends on the length of the key being used to encrypt data. Each of these subkeys is used for 16 encryption rounds. Learn faster with spaced repetition.
What form of cryptography is best suited for bulk encryption because it is so fast. A shared private key. DES Encryption Algorithm.
Every single question on the CISSP exam is a four. DES encryption uses a 56-bit key to encrypt the content and is now considered to be highly insecure. Key length is measured in bits.
Developed in the early 1970s at IBM and based on an earlier design by Horst Feistel the algorithm was. Encryption Strength is based on a Strength of Algorithm b Secrecy of key c Length of key d All of the above 72. The Data Encryption Standards DES 56-bit key is no longer considered adequate in the face of modern cryptanalytic techniques and supercomputing power.
Key values must be used only once. This is a Data Encryption Standard that is the asymmetric key generation for the encryption of digital data in cryptography. Test your knowledge of CISSP with these multiple choice questions.
Subkeys are generated by selecting and permuting parts of the key as defined by the DES algorithm. Therefore its short key length of 56 bits of character criticized from the beginning or starting makes it too insecure or safe for most current applications to use it has been highly influential in the advancement of modern cryptography. DES Weak Keys DES uses 16 48-bits keys generated from a master 56-bit key 64 bits if we consider also parity bits Weak keys.
Keys make the same sub-key to be generated in more than one round. Study Ch 6 flashcards from Josh Selkirks class online or in Brainscapes iPhone or Android app.
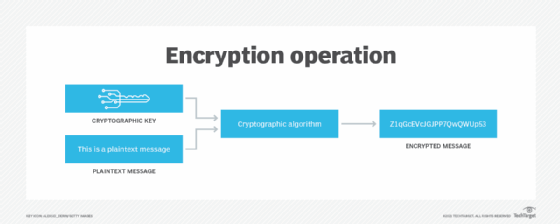
What Is An Encryption Key Definition From Searchsecurity
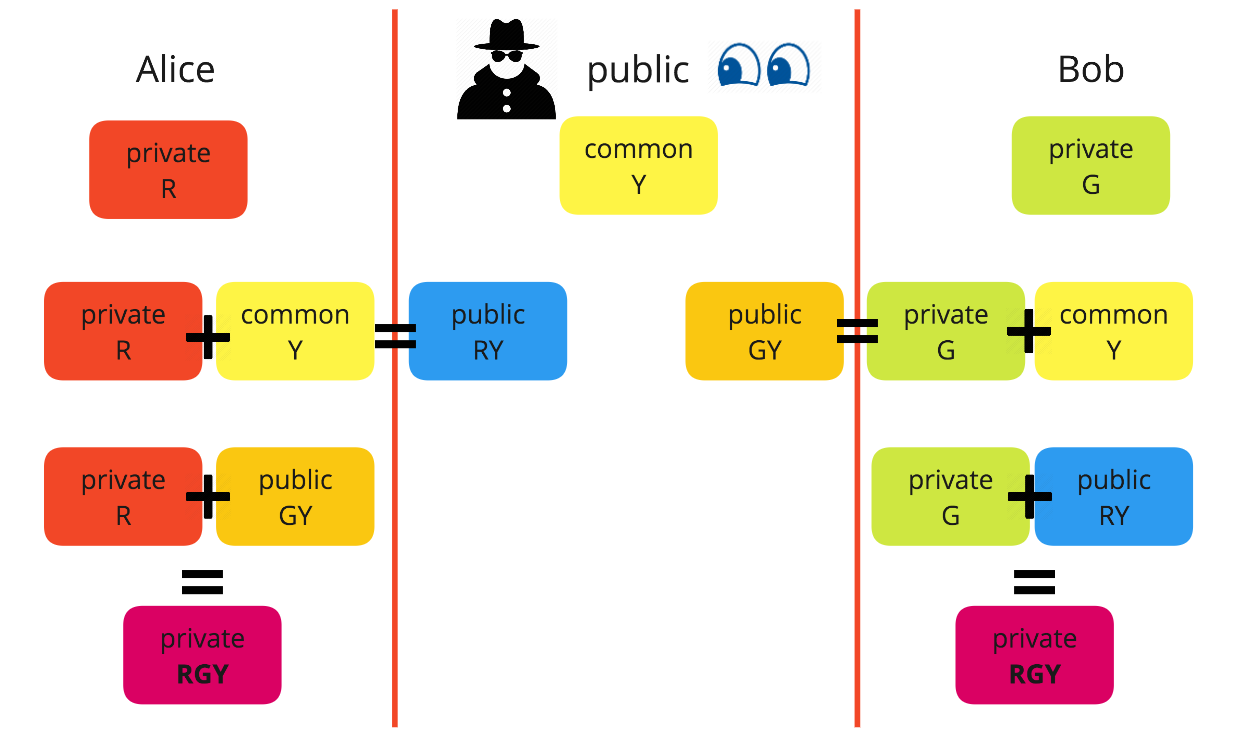
What Are Encryption Keys And How Do They Work By Dominic Fraser Codeclan Medium

What Are Encryption Keys And How Do They Work By Dominic Fraser Codeclan Medium
No comments for "Des Uses Which of the Following Encryption Key Length"
Post a Comment